Here's a mystery which I don't have time now to investigate, but I want to remember it for later.
Matlab has a constant open connection with.. itself.. through ports 4079 and 4080. All I can find is that 4080 is associated with something called "lorica", and 4079 with "SANtools". SANtools is a some sort of general utility for disc access, network storage.. I don't know what. It's familiar, I've encountered SANtools somewhere before, but can't remember. I have no idea what "lorica" could be.
Later.
Wednesday, April 13, 2011
tubely
I got an interesting email this morning - actually two of them. They were spam on my gmail account, which is interesting because I almost never get spam on that account. They were sent from the account of someone I know incidentally - actually by way of two incidents. That's a funny story, I'll tell it now, in parentheses:
(I go to a Taekwondo club, and most of the other people who go there are like me, normal slobs, not genuine atheletes or fighters, though there are many of those. Anyways, one of the people I had conversed with a few times was the mother of a child student, who would come to classes when her son was there. So, okay, we "knew" one another, saw eachother maybe once every week or two. So then, last summer, I'm shopping for a piano, looking at Craigslist ads. I see a total of 4 pianos. The second one (I bought the 3rd), I show up at the person's house to check it out - and it's the lady from Taekwondo. Very weird, in a city of a million people, that 1/4 piano ads answered contain a person you know. Oh well, that's the story.)
So, I'm apparently on this lady's email contacts list because of the piano interaction. She must have fallen for this Tubely thing - I'm still not sure exactly what Tubely is - and it dumped "invites" to everyone on her contacts list. It sounds like this is the typical Tubely MO.
The interesting thing about the emails (I got two simultaneous copies of the invite) is that they contained the sender's IP address. I have no idea why. I knew it was the lady's work address because 1) I know that she works at another Harvard-affiliated research institute, and 2) the address resolved to another computer on the Harvard network.
The emails were sent around 7:40am today, so she gets to her office at least by 7:40am. It's creepy that spam can reveal that sort of detail about you. Embarrassing and creepy.
And, it seems pretty weird, that spam would want to be giving out your exact location on the internet, through a Webmail service. Maybe it's an effort to *not* look like spam, by showing that you originate from the actual sender, as if IP addresses are obviously familiar or not. Oh well, who knows.
(I go to a Taekwondo club, and most of the other people who go there are like me, normal slobs, not genuine atheletes or fighters, though there are many of those. Anyways, one of the people I had conversed with a few times was the mother of a child student, who would come to classes when her son was there. So, okay, we "knew" one another, saw eachother maybe once every week or two. So then, last summer, I'm shopping for a piano, looking at Craigslist ads. I see a total of 4 pianos. The second one (I bought the 3rd), I show up at the person's house to check it out - and it's the lady from Taekwondo. Very weird, in a city of a million people, that 1/4 piano ads answered contain a person you know. Oh well, that's the story.)
So, I'm apparently on this lady's email contacts list because of the piano interaction. She must have fallen for this Tubely thing - I'm still not sure exactly what Tubely is - and it dumped "invites" to everyone on her contacts list. It sounds like this is the typical Tubely MO.
The interesting thing about the emails (I got two simultaneous copies of the invite) is that they contained the sender's IP address. I have no idea why. I knew it was the lady's work address because 1) I know that she works at another Harvard-affiliated research institute, and 2) the address resolved to another computer on the Harvard network.
The emails were sent around 7:40am today, so she gets to her office at least by 7:40am. It's creepy that spam can reveal that sort of detail about you. Embarrassing and creepy.
And, it seems pretty weird, that spam would want to be giving out your exact location on the internet, through a Webmail service. Maybe it's an effort to *not* look like spam, by showing that you originate from the actual sender, as if IP addresses are obviously familiar or not. Oh well, who knows.
Tuesday, March 29, 2011
TeliaSonera
For the first time in a while, saw an outgoing packet that I didn't recognize.
It was a TCP packet sent to 213.155.157.32. This seems to be part of the telia.net domain, though this address doesn't actually have a domain name. Telia is a Swedish IP that extends throughout Europe. Hostsearch says the address is maintained by Akamai, which is based here in Cambridge MA, but that it's located in London - so this is an Akamai International host, accessed through the Telia network. The packet was sent by one of those generic svchost.exe processes, and I didn't notice it in time to see if netstat could have told me anything else.
The host has open http ports - my packet was sent to port 80, so maybe it was an attempt at opening an http session. Maybe some Microsoft component was checking for an update - I've noticed before that Microsoft updates are often hosted on Akamai servers - but it's weird that it tried with a single packet and gave up. Other option (more likely maybe) is that it was a long delayed "close connection" packet, from a website I had opened much earlier - the web browser had been closed for a while, though I don't remember how long it had been.
The packet was sent from port 22095. This doesn't appear to be associated with anything interesting...
Oh well, this was pretty boring.
It was a TCP packet sent to 213.155.157.32. This seems to be part of the telia.net domain, though this address doesn't actually have a domain name. Telia is a Swedish IP that extends throughout Europe. Hostsearch says the address is maintained by Akamai, which is based here in Cambridge MA, but that it's located in London - so this is an Akamai International host, accessed through the Telia network. The packet was sent by one of those generic svchost.exe processes, and I didn't notice it in time to see if netstat could have told me anything else.
The host has open http ports - my packet was sent to port 80, so maybe it was an attempt at opening an http session. Maybe some Microsoft component was checking for an update - I've noticed before that Microsoft updates are often hosted on Akamai servers - but it's weird that it tried with a single packet and gave up. Other option (more likely maybe) is that it was a long delayed "close connection" packet, from a website I had opened much earlier - the web browser had been closed for a while, though I don't remember how long it had been.
The packet was sent from port 22095. This doesn't appear to be associated with anything interesting...
Oh well, this was pretty boring.
Friday, March 25, 2011
How To Escape the Web
I have finally found a browser configuration that can reliably keep me from screwing around on the internet.
For a while I've had the Leechblock add-on for Firefox, which lets me dynamically (i.e. on-the-spot) add a site to a list, and then keep me from seeing it for some period of time. But I figured out early on that I could remove sites from the list with just a little work. Apparently, I just didn't know how to use Leechblock to the fullest of its abilities, because it's also possible to set it so that no changes at all to its configuration - except for adding addresses - are possible outside certain circumstances, which can be made very restrictive.
So, with Firefox, I am now prohibited from visiting my favorite places to read, visiting my favorite forums, and periodically checking Facebook to make sure that, still, no one has left me any messages.
But that leaves IE, which I quickly discovered is basically un-uninstallable. You can roll back to earlier versions, but you cannot, without more expertise than I have, remove it from XP. So I persisted this way for a while, with an old version of IE that at least made me nervous to go wandering around the web, for fear of Java trojans. I could sneak over to stupid IE to check for Facebook messages, or to see what the others were talking about on the forums, or to see what country was on fire today. I was basically controlling myself relatively well, but still not satisfied.
Solution: rather than try and figure out whether there's some Leechblock equivalent for IE, I rolled IE back up to the current version, went into the "content advisor" settings, and told it not to let me visit any websites that I haven't already rated as okay. I'm not even sure what a content advisor rating is - I was just testing to see what the setting did. It prevented me from looking at basically any website at all, making IE useless. But the key is that the content advisor has a password option, so that without the password you can't change the settings.
I set the password to something I made up on the spot, and I have no idea now what it was. It was actually a word, something like arduvon or.. I remembered it for a few minutes afterwards, and worried that I had memorized it, but it's gone!
I'm not completely protected, however. I could always download Chrome or something else, or roll IE back again. The first option can be prevented by just adding the Chrome site to the Leechblock list.
Anyways, I'm pretty satisfied with this.
For a while I've had the Leechblock add-on for Firefox, which lets me dynamically (i.e. on-the-spot) add a site to a list, and then keep me from seeing it for some period of time. But I figured out early on that I could remove sites from the list with just a little work. Apparently, I just didn't know how to use Leechblock to the fullest of its abilities, because it's also possible to set it so that no changes at all to its configuration - except for adding addresses - are possible outside certain circumstances, which can be made very restrictive.
So, with Firefox, I am now prohibited from visiting my favorite places to read, visiting my favorite forums, and periodically checking Facebook to make sure that, still, no one has left me any messages.
But that leaves IE, which I quickly discovered is basically un-uninstallable. You can roll back to earlier versions, but you cannot, without more expertise than I have, remove it from XP. So I persisted this way for a while, with an old version of IE that at least made me nervous to go wandering around the web, for fear of Java trojans. I could sneak over to stupid IE to check for Facebook messages, or to see what the others were talking about on the forums, or to see what country was on fire today. I was basically controlling myself relatively well, but still not satisfied.
Solution: rather than try and figure out whether there's some Leechblock equivalent for IE, I rolled IE back up to the current version, went into the "content advisor" settings, and told it not to let me visit any websites that I haven't already rated as okay. I'm not even sure what a content advisor rating is - I was just testing to see what the setting did. It prevented me from looking at basically any website at all, making IE useless. But the key is that the content advisor has a password option, so that without the password you can't change the settings.
I set the password to something I made up on the spot, and I have no idea now what it was. It was actually a word, something like arduvon or.. I remembered it for a few minutes afterwards, and worried that I had memorized it, but it's gone!
I'm not completely protected, however. I could always download Chrome or something else, or roll IE back again. The first option can be prevented by just adding the Chrome site to the Leechblock list.
Anyways, I'm pretty satisfied with this.
Friday, January 21, 2011
yandex.ru
Another boring Sitemeter post. I'm so sorry.
Several interesting visitors recently, though I haven't kept notes and have forgotten the names of several. Someone in France came here and spent something like an hour viewing several dozen pages, I don't know why - they came in through the MS-WBT server page, though.
Someone came here through my link in Facebook, which never happens, and he looked at a few pages. I know who it was, but I won't embarrass him.
Anyway, page views are up for some reason - every day or two, someone flips through several pages, I don't know why that's happening now but not before - the MS-WBT page isn't changed, nothing is. Random winter boredom maybe?
Today there was a visitor about whom Sitemeter seemed to know nothing at all. I was curious, so tracerouted the entire IP block, and it led back to a cluster of sites named yandex.ru. This, apparently, is the Russian Google, a search engine suite. I don't know what hit the site, exactly, but maybe it was a yandexbot - the Googlebot comes every few days or weeks, maybe the yandexbot will start dropping by.
Anyways, that's pretty boring. Sorry.
Several interesting visitors recently, though I haven't kept notes and have forgotten the names of several. Someone in France came here and spent something like an hour viewing several dozen pages, I don't know why - they came in through the MS-WBT server page, though.
Someone came here through my link in Facebook, which never happens, and he looked at a few pages. I know who it was, but I won't embarrass him.
Anyway, page views are up for some reason - every day or two, someone flips through several pages, I don't know why that's happening now but not before - the MS-WBT page isn't changed, nothing is. Random winter boredom maybe?
Today there was a visitor about whom Sitemeter seemed to know nothing at all. I was curious, so tracerouted the entire IP block, and it led back to a cluster of sites named yandex.ru. This, apparently, is the Russian Google, a search engine suite. I don't know what hit the site, exactly, but maybe it was a yandexbot - the Googlebot comes every few days or weeks, maybe the yandexbot will start dropping by.
Anyways, that's pretty boring. Sorry.
Friday, December 31, 2010
WebSense
This is kind of interesting.
Being on the private network and all, I can't see the main stream of internet traffic - or, I don't know how to watch it from an external host, same thing. Anyways, I am reduced to watching Sitemeter to see if anything interesting pops up there. So we get the Italia thing from last time.
Sitemeter tells me the referring URL for most visitors to this site. 98% of them are referred from Google, because they've searched for MS-WBT-SERVER and that April page is the top return for that search. The ones that aren't from there are the interesting ones. Today I get the following referral:
http://10.237.125.90:15871/cgi-bin/blockOptions.cgi?ws-session=1817507749
An IP address starting with 10.* is a private network address - so at first I thought this was a referral from some site on my own network, which doesn't make any sense at all. Then, slightly more sensibly, I thought it must be a reference from within the Blogspot network. Then I gave up guessing, and Googled it.
A number of forum questions suggest that someone on a private network tried to see this site, but it (i.e. blogger.com) was blocked by WebSense software. So WebSense poked the site, found it was on its block list, and probably gave that person a notification that it was blocked - 15871 is the port used by the WebSense monitor or something, so this actually reveals (I think) the user's own IP address. The request came from an address in Tamil Nadu, India.
So, strangely enough, this is a way of getting information about a user from within a private network - get your site blocked by them, then you can see their external, public address when they attempt to connect, and their private address when WebSense bounces them off. Neat!
***
The public address sitemeter gave me was 203.99.193.* - this is registered to Cognizant Technology Solutions - long story short, Cognizant is (among other things) an outsourcing company. No way of knowing exactly what they're doing there, some sort of white collar stuff, call centers, that sort of thing.
Being on the private network and all, I can't see the main stream of internet traffic - or, I don't know how to watch it from an external host, same thing. Anyways, I am reduced to watching Sitemeter to see if anything interesting pops up there. So we get the Italia thing from last time.
Sitemeter tells me the referring URL for most visitors to this site. 98% of them are referred from Google, because they've searched for MS-WBT-SERVER and that April page is the top return for that search. The ones that aren't from there are the interesting ones. Today I get the following referral:
http://10.237.125.90:15871/cgi-bin/blockOptions.cgi?ws-session=1817507749
An IP address starting with 10.* is a private network address - so at first I thought this was a referral from some site on my own network, which doesn't make any sense at all. Then, slightly more sensibly, I thought it must be a reference from within the Blogspot network. Then I gave up guessing, and Googled it.
A number of forum questions suggest that someone on a private network tried to see this site, but it (i.e. blogger.com) was blocked by WebSense software. So WebSense poked the site, found it was on its block list, and probably gave that person a notification that it was blocked - 15871 is the port used by the WebSense monitor or something, so this actually reveals (I think) the user's own IP address. The request came from an address in Tamil Nadu, India.
So, strangely enough, this is a way of getting information about a user from within a private network - get your site blocked by them, then you can see their external, public address when they attempt to connect, and their private address when WebSense bounces them off. Neat!
***
The public address sitemeter gave me was 203.99.193.* - this is registered to Cognizant Technology Solutions - long story short, Cognizant is (among other things) an outsourcing company. No way of knowing exactly what they're doing there, some sort of white collar stuff, call centers, that sort of thing.
Tuesday, December 21, 2010
Italia
Oh, also I am always watching Sitemeter, keeping track of how many people are coming to check out my invaluable MS WBT tips. Somebody on an Italian network actually seems to have searched this site out by name, strangely enough: they Googled the terms "internet what i am going to learn today", which is pretty weird. May have just been a coincidence, but I think they were looking for me.
Sitemeter doesn't give the whole IP address of the visitor, just the prefixes, and in this case it couldn't be certain where the visitor was coming from. I tracerouted the whole block, though, and they all belong to the Telecom Italia backbone, called "Seabone".
So today I learned that Telecom Italia's international backbone is called Seabone.
Sitemeter doesn't give the whole IP address of the visitor, just the prefixes, and in this case it couldn't be certain where the visitor was coming from. I tracerouted the whole block, though, and they all belong to the Telecom Italia backbone, called "Seabone".
So today I learned that Telecom Italia's international backbone is called Seabone.
Publication Report 2010
My internet research has dwindled to nothing!
Meanwhile, this year's publication history:
Published manuscripts: 2
Submitted manuscripts: 0
In-preparation manuscripts: 1
Abstracts submitted: 2
Conference papers written: 2
Conference presentations: 1
Invited lectures: 1
SUBMITTED MANUSCRIPTS = 0.0, this isn't so good. I have a waiting list of whatever comes right before "in-preparation", though.
Okay, what did I learn today:
Well, I built a model of adapted image quality (blur/normal/sharp) matching yesterday, and fixed it up today. It does just what it should: it "normalizes" when adapted to one or another type of input, though for now its starting point is "blank adapted" which isn't quite right. It also displays the loss of blur/sharp gain that I found in the matching experiment (which accounts for 4 of the above objects: paper in preparation, abstract accepted, presentation and lecture given).
The model is your basic contrast transducer array, a set of Foley functions (Stromeyer-Foley, Naka-Rushton, etc.) with thresholds set by a standard function. I've built it several times before, but this is the first time I came up with a good way of implementing the adaptation part. This is the transducer function, with w in the denominator standing in for some added (only added, yes) gain control function:
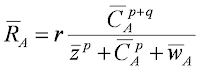
The idea is that the system wants R to be kept relatively constant, at a particular level above threshold but not terribly near saturation - but C keeps changing, so how to keep R in that ideal range? Yes, we adapt, and here adaptation basically means setting the value of w. That's easy to do, just solve for w. This introduces probably the most important free parameter in the model, R, because I don't know what it should be, though I have a good idea of the range, and luckily the thing only really behaves if I put it in that range. So okay, it works!
So what I learned is that the third time you build something, it might actually work. From now on I need to make sure to build everything at least three times.
Meanwhile, this year's publication history:
Published manuscripts: 2
Submitted manuscripts: 0
In-preparation manuscripts: 1
Abstracts submitted: 2
Conference papers written: 2
Conference presentations: 1
Invited lectures: 1
SUBMITTED MANUSCRIPTS = 0.0, this isn't so good. I have a waiting list of whatever comes right before "in-preparation", though.
Okay, what did I learn today:
Well, I built a model of adapted image quality (blur/normal/sharp) matching yesterday, and fixed it up today. It does just what it should: it "normalizes" when adapted to one or another type of input, though for now its starting point is "blank adapted" which isn't quite right. It also displays the loss of blur/sharp gain that I found in the matching experiment (which accounts for 4 of the above objects: paper in preparation, abstract accepted, presentation and lecture given).
The model is your basic contrast transducer array, a set of Foley functions (Stromeyer-Foley, Naka-Rushton, etc.) with thresholds set by a standard function. I've built it several times before, but this is the first time I came up with a good way of implementing the adaptation part. This is the transducer function, with w in the denominator standing in for some added (only added, yes) gain control function:
The idea is that the system wants R to be kept relatively constant, at a particular level above threshold but not terribly near saturation - but C keeps changing, so how to keep R in that ideal range? Yes, we adapt, and here adaptation basically means setting the value of w. That's easy to do, just solve for w. This introduces probably the most important free parameter in the model, R, because I don't know what it should be, though I have a good idea of the range, and luckily the thing only really behaves if I put it in that range. So okay, it works!
So what I learned is that the third time you build something, it might actually work. From now on I need to make sure to build everything at least three times.
Monday, November 15, 2010
MS WBT SERVER 2
This site has been getting more than 20 hits/day because of this post from back in April. Basically, all it does is describe some packets that were sent to a port used by the service MS WBT SERVER. It supplies a critical piece of information for those wishing to find out what, exactly, MS WBT SERVER is: "this is the port used by the 'Remote Desktop' utility in windows". There, I've done it again! Now I should start getting twice as many hits.
Sitemeter says that something like 98% of those hits leave the site immediately without looking at anything, probably because people immediately recognize that there's nothing useful here at all. But they keep coming, more every week, more every month! Every once in a while someone goes and looks at one of the indices on the right side of the page, maybe thinking, "ah, there's where something useful might be hidden!" Usually they leave right after that, but it's interesting anyways. I haven't gotten any comments on any of my old comedic dialogues unfortunately.


Virtually every one of these visits was referred from google.com, from a search for MS WBT SERVER.
For comparison, here's an old record from a couple of years ago.
Sitemeter says that something like 98% of those hits leave the site immediately without looking at anything, probably because people immediately recognize that there's nothing useful here at all. But they keep coming, more every week, more every month! Every once in a while someone goes and looks at one of the indices on the right side of the page, maybe thinking, "ah, there's where something useful might be hidden!" Usually they leave right after that, but it's interesting anyways. I haven't gotten any comments on any of my old comedic dialogues unfortunately.

Virtually every one of these visits was referred from google.com, from a search for MS WBT SERVER.
For comparison, here's an old record from a couple of years ago.
Monday, October 18, 2010
ARP
One small thing, which I don't have on hand - the other night, I switched on the network monitor and saw an exchange I'd never seen before: ARKIV (my computer) sent an ARP packet to Jingping's computer, which is on the same local network - immediately, her computer responded with two UDP skype packets. ARKIV's skype was turned off. Is skype constantly checking incoming messages to see if they come from an address in its routing tables - in that case why was Jingping the only computer that got an ARP packet? Was the ARP packet sent by some active skype process? Mysteries, mysteries...
(These conversations suggest that skype knows enough to adjust its routing for LANs - so instead of IP addresses it needs to be routing to MAC addresses, or something.)
(These conversations suggest that skype knows enough to adjust its routing for LANs - so instead of IP addresses it needs to be routing to MAC addresses, or something.)
Wednesday, October 13, 2010
Audio
Ok, here's something slightly interesting. It has to do with Skype - the only traffic I can see here that isn't building business, or something I'm doing (webpages, ftp, updates, etc.) is Skype, so I guess that's what I live with until I go figure out something new.
Anyways, I've mentioned before about how my Skype account seems to use port 34268 to advertise its existence - UDP packets go in and out through that port, and sometimes a link gets established with one of the associated addresses, and a conversation starts - i.e. my computer gets used as a relay in the Skype network. Sometimes I see the UDP packets go out, looking for another node, and nothing comes back - they go out a few more times, and give up.
So, what I noticed is that tonight, my computer is sending RTP packets, which I haven't seen before, rather than UDP packets. RTP is apparently used for transferring video and audio, especially with VOIP applications. So, Skype is looking for someone accepting video/audio streams, trying to establish an RTP network? I have no idea.
Each of those RTP messages was reciprocated with a UDP response, by the way. Nothing else followed, however - there's a single conversation going on through Skype, leisurely exchanging TCP packets every few dozen seconds, so I would assume this is a text conversation - but it's a one-sided conversation, since my computer is communicating only with one other address! If I were relaying a conversation, I should see connections with two other hosts, not one. Maybe some sort of routing table content is being transferred, updated, etc., very slowly?
That's all I've got.
Anyways, I've mentioned before about how my Skype account seems to use port 34268 to advertise its existence - UDP packets go in and out through that port, and sometimes a link gets established with one of the associated addresses, and a conversation starts - i.e. my computer gets used as a relay in the Skype network. Sometimes I see the UDP packets go out, looking for another node, and nothing comes back - they go out a few more times, and give up.
So, what I noticed is that tonight, my computer is sending RTP packets, which I haven't seen before, rather than UDP packets. RTP is apparently used for transferring video and audio, especially with VOIP applications. So, Skype is looking for someone accepting video/audio streams, trying to establish an RTP network? I have no idea.
Each of those RTP messages was reciprocated with a UDP response, by the way. Nothing else followed, however - there's a single conversation going on through Skype, leisurely exchanging TCP packets every few dozen seconds, so I would assume this is a text conversation - but it's a one-sided conversation, since my computer is communicating only with one other address! If I were relaying a conversation, I should see connections with two other hosts, not one. Maybe some sort of routing table content is being transferred, updated, etc., very slowly?
That's all I've got.
Sunday, October 03, 2010
Private networks are boring
Just as the title says. Since moving into this new apartment, I've been viewing the internet only from within private networks, at home or in the lab. It's very boring. Here, as there, I see absolutely nothing but the browsing traffic and attendance updates between the hosts and the server. Nothing from outside, ever.
I haven't done anything, learned anything internet-wise, since moving here. This is the reason.
Before, when I had that public Comcast address, it was like living on the street, and all the random scans and searches that passed by every other minute were like other street people, bumping around and looking for somebody to take advantage of, or just exploring as I was doing, scanning this or that node, looking for something interesting.
The private network is like living in... an apartment building, or a suburban neighborhood, where all you ever see are your neighbors, and all they're ever doing is routine, everyday, necessary things, which aren't interesting at all except in that they're being done and that they're done every day, routinely - routine has a quality all its own, but it's not much fun to watch.
I need to figure out how to watch traffic from other hosts. It's time to expand my abilities.
I haven't done anything, learned anything internet-wise, since moving here. This is the reason.
Before, when I had that public Comcast address, it was like living on the street, and all the random scans and searches that passed by every other minute were like other street people, bumping around and looking for somebody to take advantage of, or just exploring as I was doing, scanning this or that node, looking for something interesting.
The private network is like living in... an apartment building, or a suburban neighborhood, where all you ever see are your neighbors, and all they're ever doing is routine, everyday, necessary things, which aren't interesting at all except in that they're being done and that they're done every day, routinely - routine has a quality all its own, but it's not much fun to watch.
I need to figure out how to watch traffic from other hosts. It's time to expand my abilities.
Thursday, September 16, 2010
Tuesday, July 06, 2010
back
okay, june was a busy month, and it had absolutely nothing to do with me learning anything at all about the internet. and, lately, i have lost interest in the topic. but i'm sure it will come back! i'll be moving to a new apartment by and by, where the internet is apparently distributed by a local network run by the building manager - i.e. i'll be plugging into a LAN to get outside. so, first, i'll have to find out what i can and can't do from there, but it will also be interesting to try and figure out how the building's network is put together. i'm guessing, however, that i won't have my own IP address any longer, which will be a plus and a negative when it comes to exploration.
Friday, May 21, 2010
skyping
watching skype here in the lab. sending a few messages from here to jingping. interesting thing is that i don't have a direct link to her. instead, skype only reports having connections with computers at NYU - several of them, six different hosts. maybe they're using me as a relay? or, i could be part of a similar set of harvard-located hosts. here, instead of 36268 or whatever it is at home, the port being used by skype for those UDP messages is always 38253. i also see that i'm sending to each of those NYU hosts from the same port, but receiving from a different port from each one. i'm guessing that all these connections are for the same purpose, and that again for each of those users the port number is the same for all their connections.
oh well, more later. maybe something interesting will happen.
oh well, more later. maybe something interesting will happen.
Tuesday, May 18, 2010
chinese-american economics
unrelated to the internet, but i did realize this last night, so it may as well go down here.
i'm aware of two facts, to which we are all constantly exposed by various media:
A. the US buys lots of stuff from China, more than China buys from the US, so there's a trade imbalance. this means the Chinese are stuck with extra $$ that they can't spend, so they loan it back to the US to continue the cycle.
B. the Chinese 元 is tied, in part, to the US $$.
i knew these things already, but didn't realize they were directly related. but they are - and so far i think it's a one-way relationship, in that A) makes B) necessary. i understood it in terms of the following cycle:
1. China companies manufacture goods
2. US companies purchase China goods with $$
3. China companies purchase US goods with the $$ they accumulated
4. China companies have $$ leftover
5. China companies need to pay for domestic costs and profit, but can't spend $$ in China
6. China companies give their $$ to China govt, which gives them China 元 in exchange
7. China govt loans $$ to US treasury
8. US treasury loans $$ to US banks
9. US banks loan $$ to US companies
10. (back to 2.)
this seems to work. I don't know anything about how sustainable it is, though I think I see how you could get to know, or have a strong opinion about, something like that by looking at this process in detail.
anyways, why does A lead to B? because of 6). in order for 6) to be a fair deal, so that the China companies can know they're getting exactly their dollar's worth in the trade, the $$ and the 元 should be closely linked. in essence, those $$-linked 元 are like $$ printed in Chinese form, with the actual $$ stored away as ensured value, like gold - this is why they call $$ a reserve currency.
so apparently, this journal is entirely devoted to me figuring out things that everyone else knows already.
i'm aware of two facts, to which we are all constantly exposed by various media:
A. the US buys lots of stuff from China, more than China buys from the US, so there's a trade imbalance. this means the Chinese are stuck with extra $$ that they can't spend, so they loan it back to the US to continue the cycle.
B. the Chinese 元 is tied, in part, to the US $$.
i knew these things already, but didn't realize they were directly related. but they are - and so far i think it's a one-way relationship, in that A) makes B) necessary. i understood it in terms of the following cycle:
1. China companies manufacture goods
2. US companies purchase China goods with $$
3. China companies purchase US goods with the $$ they accumulated
4. China companies have $$ leftover
5. China companies need to pay for domestic costs and profit, but can't spend $$ in China
6. China companies give their $$ to China govt, which gives them China 元 in exchange
7. China govt loans $$ to US treasury
8. US treasury loans $$ to US banks
9. US banks loan $$ to US companies
10. (back to 2.)
this seems to work. I don't know anything about how sustainable it is, though I think I see how you could get to know, or have a strong opinion about, something like that by looking at this process in detail.
anyways, why does A lead to B? because of 6). in order for 6) to be a fair deal, so that the China companies can know they're getting exactly their dollar's worth in the trade, the $$ and the 元 should be closely linked. in essence, those $$-linked 元 are like $$ printed in Chinese form, with the actual $$ stored away as ensured value, like gold - this is why they call $$ a reserve currency.
so apparently, this journal is entirely devoted to me figuring out things that everyone else knows already.
Sunday, May 16, 2010
what is in my packet net?
a boring post, to start: i'm just going to go through the list of what packets i caught during a 780 second capture. skype was on, as was xdict and its incessant search for the kingsoft mothership, which is currently routed to ARKIV itself.
first on the list:
p3nlhg43c081.shr.prod.phx3.secureserver.net
robtex suggests that this is some sort of porn locus, responsible for porn spam and who knows what else. sent one packet from their http port 80 to my port 19246, which is for i don't know.
next:
multiple, periodic IGMP signals, labeled "membership report". i see this all the time, sent to 239.255.255.250. apparently, this is just to establish my presence on the network, so that the routers and other whoever know i'm here.
next:
there were 8 apparent skype contacts through port 34268. what i understand is that this is how different skype hosts find eachother. what i don't understand is why for me it's always 34268, while its always different ports for the others. could it be that for them it's always their number? maybe i'm a member of a particular skype class - the port 34268 class. really, i have no idea. these are always UDP packets, call and response, usually just once, always intiated by ARKIV. and, as i mentioned before, i see them even when skype is off, but ARKIV doesn't respond then.
next:
BROWSER: host announcement. i assume this is something like the "membership report" above, but i don't know what makes it different - ARKIV runs a browser service, and there are browser elections, to select a browser which will keep track of all the potential browsers.. argh.
next:
here is a succinct description: packet from 190.2.29.193, originating from Argentina, from port 1217 to 1434 - 1434 was the way in for something called the SQL slammer worm. SQL is a microsoft database server program - what i received was a single SSRP packet, which is a protocol specially designed for use with the SQL thingie. anyways, one hit, nothing else (presumably i am not running an SQL database server).
so really, that's it. i found a paper on principles of routing in between networks, but haven't read it yet. my learning progress is stalling.
first on the list:
p3nlhg43c081.shr.prod.phx3.secureserver.net
robtex suggests that this is some sort of porn locus, responsible for porn spam and who knows what else. sent one packet from their http port 80 to my port 19246, which is for i don't know.
next:
multiple, periodic IGMP signals, labeled "membership report". i see this all the time, sent to 239.255.255.250. apparently, this is just to establish my presence on the network, so that the routers and other whoever know i'm here.
next:
there were 8 apparent skype contacts through port 34268. what i understand is that this is how different skype hosts find eachother. what i don't understand is why for me it's always 34268, while its always different ports for the others. could it be that for them it's always their number? maybe i'm a member of a particular skype class - the port 34268 class. really, i have no idea. these are always UDP packets, call and response, usually just once, always intiated by ARKIV. and, as i mentioned before, i see them even when skype is off, but ARKIV doesn't respond then.
next:
BROWSER: host announcement. i assume this is something like the "membership report" above, but i don't know what makes it different - ARKIV runs a browser service, and there are browser elections, to select a browser which will keep track of all the potential browsers.. argh.
next:
here is a succinct description: packet from 190.2.29.193, originating from Argentina, from port 1217 to 1434 - 1434 was the way in for something called the SQL slammer worm. SQL is a microsoft database server program - what i received was a single SSRP packet, which is a protocol specially designed for use with the SQL thingie. anyways, one hit, nothing else (presumably i am not running an SQL database server).
so really, that's it. i found a paper on principles of routing in between networks, but haven't read it yet. my learning progress is stalling.
China 222 part 3
not much going on - watched a couple of scans, but haven't studied much. saw the same 222.45.112.59 scan, on ports 8085, 9415, 3246, 9090, and 8090. it probably spins around every few hours, from what others have said on ipillion.com. got a single hit from 222.169.118.106, another chinese location, on a single port. this one actually had a domain name: 106.118.169.222.broad.bc.jl.dynamic.163data.com.cn.
read a bit about routing a few days ago, and got a bit of a sense for it, but not really - but then, Jason gave me a great piece of information that I hadn't gleaned yet from my browsing: routers and other computers broadcast their addresses and routing information across the networks. this is how routing tables get their information. i'm still not totally clear on it, but i'll figure it out.
Jason also suggested i get around to learning how to use linux, and install at least a virtual version of it to use, since that's what real internet people do. i may do that, if only for the fun of it.
but anyways, nothing much learned lately. slow week.
read a bit about routing a few days ago, and got a bit of a sense for it, but not really - but then, Jason gave me a great piece of information that I hadn't gleaned yet from my browsing: routers and other computers broadcast their addresses and routing information across the networks. this is how routing tables get their information. i'm still not totally clear on it, but i'll figure it out.
Jason also suggested i get around to learning how to use linux, and install at least a virtual version of it to use, since that's what real internet people do. i may do that, if only for the fun of it.
but anyways, nothing much learned lately. slow week.
Wednesday, May 12, 2010
DNS server
ok, just got home, thought i'd look at the monitor.
nothing much going on, except i see two reciprocated queries to an address i recognize as something that comes up often as a comcast address - both packets were DNS packets, which as i take it are a type of UDP packet, or maybe not. anyways, i guessed that the address must be a DNS server. since i usually am not using the web browser when i look at the monitor, i wouldn't have noticed this before.
so, i google it and sure enough, 68.87.71.230 is the primary comcast DNS server for massachusetts.
now, one of the queries was for the institute FTP server, which i used to get a file. the other was for tools.google.com, which i do not like, because i did not know google was running something in the background on my computer. the address was then contacted and some packets were traded, a couple were HTTP messages saying "update". i'm going to find out what it is, and kill it. (could be Chrome which i have installed but don't use. i don't have any google plugins or anything for firefox. Chrome must go.)
nothing much going on, except i see two reciprocated queries to an address i recognize as something that comes up often as a comcast address - both packets were DNS packets, which as i take it are a type of UDP packet, or maybe not. anyways, i guessed that the address must be a DNS server. since i usually am not using the web browser when i look at the monitor, i wouldn't have noticed this before.
so, i google it and sure enough, 68.87.71.230 is the primary comcast DNS server for massachusetts.
now, one of the queries was for the institute FTP server, which i used to get a file. the other was for tools.google.com, which i do not like, because i did not know google was running something in the background on my computer. the address was then contacted and some packets were traded, a couple were HTTP messages saying "update". i'm going to find out what it is, and kill it. (could be Chrome which i have installed but don't use. i don't have any google plugins or anything for firefox. Chrome must go.)
Subscribe to:
Posts (Atom)
